Consider the following scenario. You are behind a strict firewall that drops any kind of outgoing traffic apart from web browsing. Technically, it means that only two ports are open for outgoing connections: 80 (http) and 443 (https). You need to access your server on the Internet via SSH on port 22 (with applications like PuTTY and WinSCP).
One of possible solutions is to use port forwarding: on your server, redirect all incoming traffic from port 443 to the port 22. Linux firewall, iptables, is extremely powerful, and allows such things to be created in just three lines.
Spent few hours trying to configure those three lines for iptables using PREROUTING, DNAT, POSTROUTING and MASQUERADE. Suddenly, I came across another solution, which was indeed genius. Configure SSH server to listen on two ports, 22 and 443!
Open /etc/ssh/sshd_config and tell SSH server to listen not only on port 22 but also 443: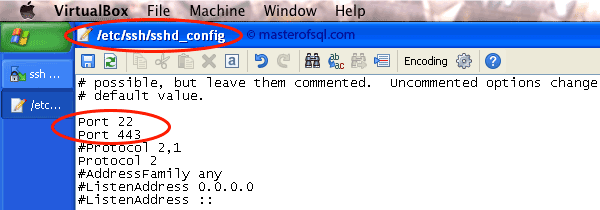
Save the file and restart SSH daemon with
service sshd restart
Now open new SSH session, but specify port 443 instead of 22: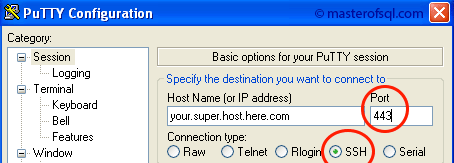
Two simplest lines will solve the problem. Of course, this is only possible if port 443 is not in use on your server. If you found this info extremely useful, you can always buy me a beer :)
2,472 total views, 1 views today